Information Security Engineering

Research Staff
-

Professor
Yuichi HAYASHI -

Associate Professor
Daisuke FUJIMOTO -

Affiliate Associate Professor
Youngwoo KIM -

Assistant Professor
Shugo KAJI -

Affiliate Assistant Professor
Hikaru NISHIYAMA
Research Areas
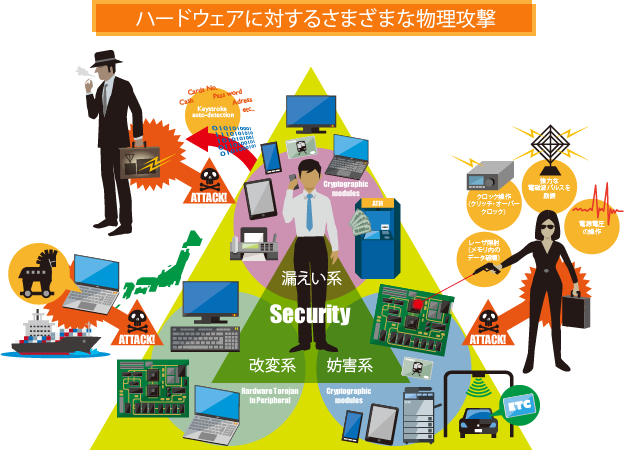
As information security becomes more important on a daily basis, physical- and upper-layer security are becoming major concerns. In fact, the ever increasing precision and price drop of measuring devices along with the increasing speed and memory of computers, enables high-level attacks that used to be technically difficult to achieve. Such attacks represent threats not only to the military and diplomatic areas, but also to commerce and industry.
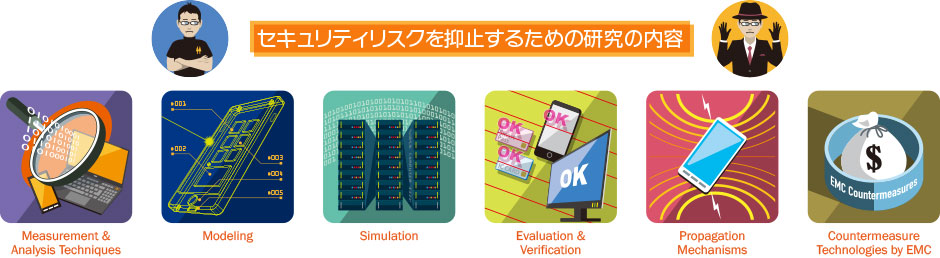
With focus on physical-layer security, the ISE Lab conducts research and development concerning information leakage mechanisms and their countermeasures, as well as research on overall system security including the upper hardware-based layer.
Evaluation and countermeasures for security compromised by leaked electronic information
Our research on security compromised by hardware information leakages has been focused on side-channel attacks over encryption modules and TEMPEST for input/output devices, such as displays and keyboards. As these threats consist of measurement and subsequent analysis of leaked electronic information, it is possible to deter these attacks by increasing the difficulty of the measurements. Measurement of electronic information can be detected by probing for electric or magnetic fields, and according to the laws of physics, the probe is able to noninvasively measure surrounding electromagnetic fields. Therefore, if it is possible to detect whether leaked electronic information has been measured using a probe, the difficulty of this measurement can be increased without bounds. From these principles, we aim to develop sensor technology that enables accurate and extensive detection of changes in electromagnetic fields caused by information measurements. In addition, to gain a deeper understanding of actual attack methods, we evaluate several types of attacks against a variety of devices.
-
Side-channel-attack sensors that cannot be physically compromised by attackers
-
Evaluation environment of information leakage
through radio waves on mobile devices
Evaluation and countermeasures for security compromised by electromagnetic interference
Intentional electromagnetic interference occurs when security is compromised by electromagnetic disturbances into the hardware of electronic devices. This interference is known as fault attack when it affects encryption modules. This security issue consists of injecting a fault and analyzing the results from the disturbance. Therefore, if the first stage of these attacks consisting of fault injection can be prevented, most of them can be rendered ineffective. Currently, fault injection mechanisms include electromagnetic signal applications, such as pulse and continuous sine waves, power supply voltage and clock manipulation and irradiation by means such as lasers, which induce faults by causing internal electronic disturbances in devices. Therefore, our goal is to deter fault injection by developing sensors that can detect electrical changes within chips and circuit boards, and any type of electrical disturbance, which can cause faulty operation both inside and outside the ICs. Moreover, as it is necessary to deeply understand real attacks to decide the sensitivity for attack detection, we recreate attacks that cause electronic disturbances and evaluate their behavior.

Evaluation environments and countermeasures for boundary expansion of fault injection and remote fault injection
Countermeasures for security compromised by changes to internal circuits
Intentional hardware changes to internal circuits can compromise security by affecting the operation and specification of electronic devices, or leaking and destroying information from the installation of a corruptive electronic/electrical circuit within the device to operate as hardware Trojan horses. As the installation of Trojan horses adds gates to the ICs and wiring to the substrates, it can be detected from changes in electric constants related to the normal operation of the devices. For this reason, we are conducting research and development on inspection methods to detect changes in electromagnetic field coupling caused by the installation of hardware Trojan horses in electronic devices and their surroundings. Furthermore, we are developing methods for devices to halt their operation when electric constants inside chips change given the presence of a Trojan horse, and working to either impede its installation or quickly detect it by using noninvasive methods. Likewise, we are studying attack scenarios considering parameters such as the timing for Trojan horse installation, its costs, and the attacker abilities.
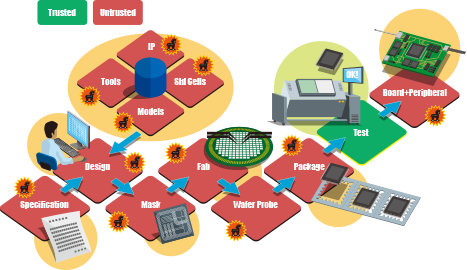
Attack scenarios of hardware Trojan horse installation
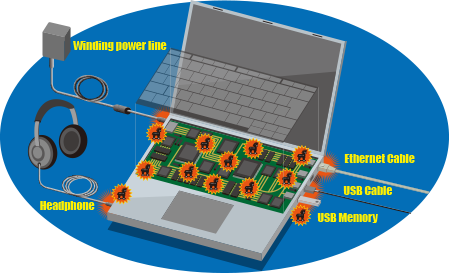
Developing detection methods for Trojan horses installed on computer circuit boards and peripheral devices
Visualization of hardware attacks and reliability of communication networks
By visualizing electromagnetic fields around hardware, we are developing countermeasures that reveal information leakage and cannot be bypassed by attackers. In addition, we are developing methods to evaluate the resistance against physical-layer attacks during the device design through large-scale electromagnetic field simulations running on supercomputers. Furthermore, we are researching design methods for communication-network devices with limited electromagnetic signal leakage from both electromagnetic compatibility and electromechanical device engineering standpoints, and high resistance to electromagnetic disturbances.
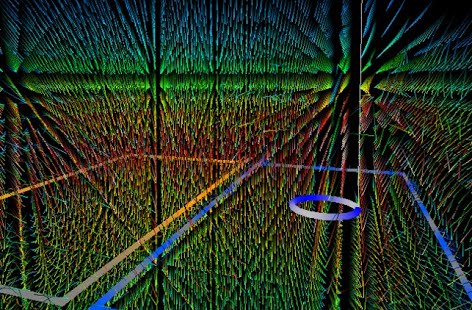
Visualizing side-channel attacks using large-scale electromagnetic field simulations
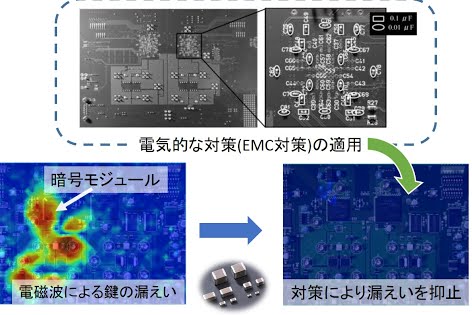
Developing information leakage suppression using inexpensive components
Key Features
In the Information Security Engineering Laboratory, we conduct research on methods to ensure hardware safety, which is the bedrock of system information security. We also conduct research to ensure the security of the entire system, including the upper layers.