Dependable System

Dependability for Algorithms, Networks and Hardware
Research Staff
-

Professor
Michiko INOUE -

Affiliate Professor
Fukuhito OOSHITA -

Affiliate Associate Professor
Wenyuan WANG -

Affiliate Associate Professor
Michihiro SHINTANI -

Assistant Professor
Ryota EGUCHI -

Assistant Professor
Taisho SASADA
| dsl-contact@is.naist.jp | |
| To the site | https://sites.google.com/view/dependablesyslab/english-home?authuser=0 |
Knowledge and Skills Required to Begin Research
Research curiosity and enthusiasm are essential, and we welcome students from both humanities and science backgrounds. Having experience with at least one programming language (either software or hardware) or being proficient in mathematics will help you start research smoothly, but beginners will also receive thorough support to progress in their research.
Laboratory Teaching Policy
Research themes are set according to each student's interests and background, starting with acquiring necessary knowledge and skills, aiming for research results that can be presented at international conferences and journals. We provide guidance to develop logical thinking, scientific verification abilities, and skills to communicate research findings to others. For research in algorithms and quantum key distribution, we represent systems using mathematical models, logically consider methods and limitations, and evaluate through theoretical analysis or simulation. In security research, we discuss vulnerabilities in programs and systems, including attack evaluation and implementation verification. For hardware research, we propose solutions based on understanding the essence of problems and evaluate through circuit simulation.
Skills Acquired Through This Research
Regardless of the research theme chosen, students will develop logical thinking and analysis skills, presentation abilities, English conversation skills, and the ability to read and write technical documents in English. Depending on the research theme, students will acquire specialized knowledge such as algorithm design and analysis capabilities, program implementation techniques, simulation evaluation skills for distributed processing/circuits/quantum computing, implementation of cutting-edge machine learning algorithms, defense techniques against vulnerabilities and hacking, and hardware design/analysis skills.
Career Opportunities
SB Intuitions Co., Ltd., Asahi Kasei, Analog Devices, OMRON, Kioxia, Cookpad, BrainPad, Cybozu, Sumitomo Electric Information Systems, Sony LSI Design, Daikin, SCREEN Holdings, DENSO, Nomura Research Institute, VIC - Visible Information Center, Fujitsu Computer Technologies, Mitsubishi Electric, Murata Manufacturing, MonotaRO, Ricoh, Renesas Electronics, ROHM, Shimane University, Ishikawa National College of Technology, Ateneo de Manila University, Prime University (Bangladesh), etc.
Research Content
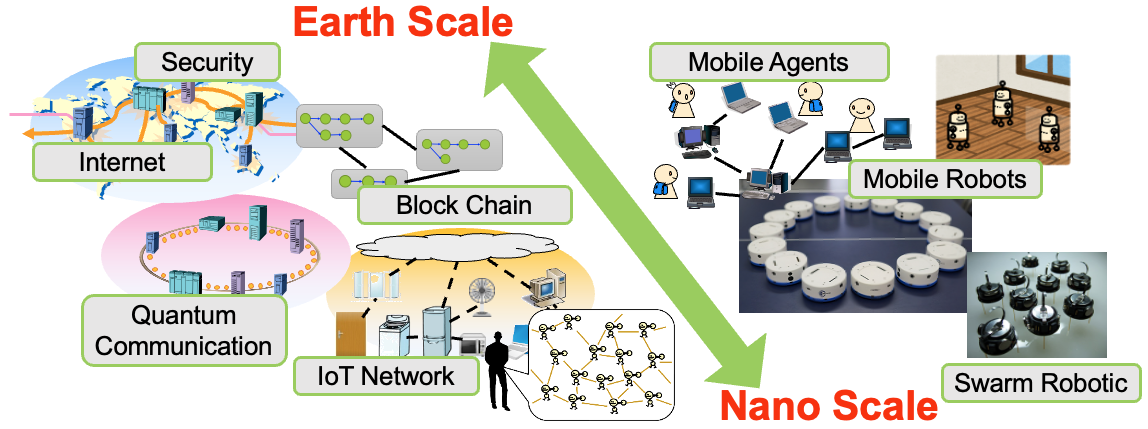
Fig1:Research Area
Today's information society is supported by advanced technologies at various levels, including applications, networks, computers, and VLSI. The Dependable System Laboratory conducts research on systems that users can rely on at all levels, including distributed systems, multicore computers, VLSI, brain-inspired computers, quantum computing, and security.
Distributed Algorithms
We focus on designing algorithms to improve the dependability and performance of various distributed systems such as the Internet, ITS, IoT, blockchain (bitcoin), sensor networks, and nano-scale systems.
- Self-stabilizing algorithms that autonomously recover from failures
- Mobile agents that autonomously move around networks
- Application of random algorithms in sequential processing to distributed algorithms
- Probabilistic analysis in natural random procedures such as random walk
- Swarm robotics
- Distributed algorithm for dynamic graphs
- Distributed ledgers used in block chains
- Population protocols for nano-scale systems
- Dynamic distributed algorithms
VLSI Dependability
Integrated circuits are core devices in various systems. The miniaturization of transistors enabling larger scale, high performance, and more power-efficient integrated circuits supports today's information society and AI advancement. However, testing integrated circuits has become increasingly complex, and reliability concerns due to transitor aging and security concerns such as hardware Trojan circuit insertion due to complicated supply chains have emerged. Furthermore, as CMOS transistor miniaturization reaches physical limits, new devices and architectures are expected, making reliability assurance a crucial challenge. Our laboratory addresses various integrated circuit dependability issues, including reliable design of memristor neural networks, improving integrated circuit security through hardware Trojan detection, and enhancing test quality using machine learning.
- Improving memristor neural network reliability through fault injection training
- Hardware Trojan detection methods using power side-channel learning consideringrandom variations
- Improving integrated circuit test quality using machine learning
Quantum Key Distribution
Quantum information science has attracted lots of attention in recent years. In particular, facing the threat from quantum computers, researchers proposed the Quantum Key Distribution (QKD), a quantum communication protocol, as a potent countermeasure. QKD uses polarization states of photons to generate secret keys, and it is able to detect and quantify any possible eavesdropping attack and ensure secure communications. However, vulnerabilities called side-channels exist in the sources and detection devices in practical QKD systems. To address such side-channels, we develop measurement-device-independent (MDI) QKD protocols and fully passive QKD sources that enable more practically secure QKD systems. Meanwhile, noisy intermediate-scale quantum devices (NISQ) saw much development in the past decade, and we are interested in exploring the new field of quantum machine learning on NISQ devices and in particular its security. Our laboratory collaborates with researchers from institutes in e.g. Canada, Spain, and Hong Kong on the following past/ongoing topics:
- Measurement-device-independent quantum key distribution protocols
- Fully passive quantum key distribution sources
- Security of quantum machine learning
Data Security/Privacy
Cyber attacks through hackers exploiting security vulnerabilities and new types of malware are increasing daily, posing serious threats to information and communication technology security. To address these cyber attacks, network security technologies to protect against communication eavesdropping and impersonation attacks, and privacy enhancement technologies to protect information contained in data are essential.
Our laboratory tackles various security and privacy challenges, including zero-trust network access to prevent information leakage via malware, privacy protection during data collection and utilization for AI model construction, and prevention of poisoning attacks against AI models themselves. In collaboration with research institutions in the United States, France, and Bangladesh, we are currently working on the following research themes:
- Zero-trust architecture design for blocking lateral movement by malware
- Secure GPS data collection method using Differential Privacy
- Contaminated data separation method for preventing AI model poisoning attacks
Research Facilities
Computing servers, autonomous distributed robot groups (150 Kilobots, 15 Khepera IV),sensor equipment
Research Achievements, Joint Research, Social Activities,and External Funding
Research achievements: See achievements list page
- Partner research institutions: Sorbonne University (France), Telecom SudParis (France), Angelo State University (United States), University of Toronto, University of Vigo, University of Hong Kong, Osaka University, Keio University, Fukui University of Technology, Hosei University
- External funding: JSPS KAKENHI, Google Cybersecurity Research Award, Kayamori Foundation of Informational Science Advancement